Decentralized finance (DeFi) platform Fei Protocol offered a $ten million bounty to online hackers so that they can negotiate and retrieve a significant slice of the stolen funds from various Rari Fuse pools worth $79,348,385.61 — nearly $80 million.
On Saturday, Fei Protocol informed its investors a good exploit across numerous Rari Capital Fuse pools while requesting the online hackers to come back the stolen funds against a $ten million bounty along with a “no questions asked” commitment.
We know about an exploit on various Rari Fuse pools. We’ve identified the main cause and stopped all borrowing to mitigate further damage.
Towards the exploiter, please pay a $10m bounty with no questions requested should you return the rest of the user funds.
— Fei Protocol (@feiprotocol) April 30, 2022
As the exact losses in the exploit weren’t formally released, DeFi investigator BlockSec’s monitoring system detected a loss of revenue in excess of $80 million — citing the main cause like a typical reentrancy vulnerability. While reentrancy bugs happen to be the primary offender in lots of exploits inside the DeFi ecosystem, the $80 million loot helps make the Fei Protocol exploit among the largest reentrancy hacks ever.
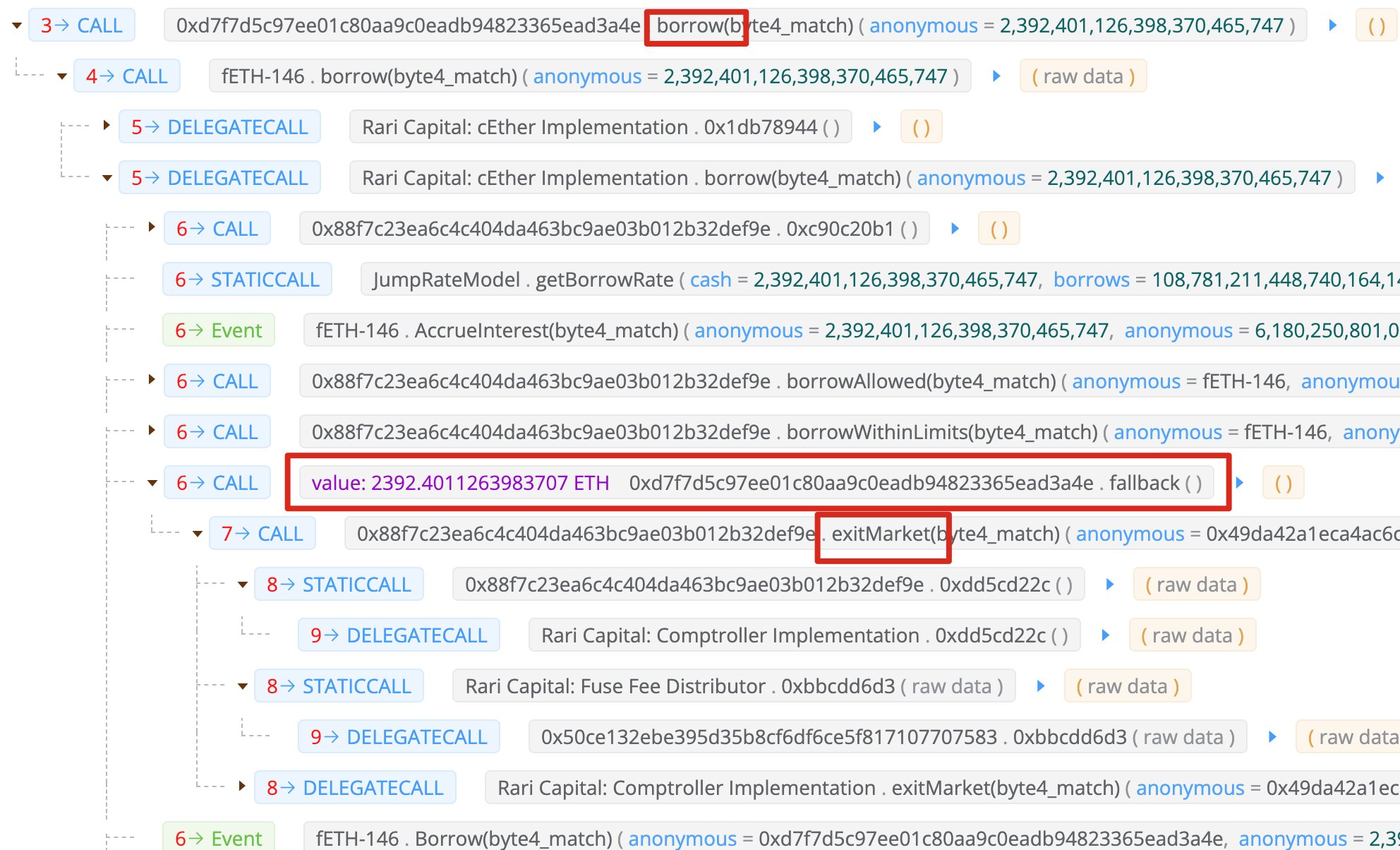
Upon further investigations, Rari developer Jack Longarzo revealed as many as six vulnerable pools (8, 18, 27, 127, 144, 146, 156) which have been temporarily stopped while an interior fix is going ahead. During the time of writing, Rari’s internal and exterior security engineers partnered with DeFi company Compound Treasury to help investigate and neutralize the hack.
Supplying further insights in to the development, blockchain investigator PeckShield narrowed lower the exploit to some reentrancy bug, which enables online hackers to utilize a function making exterior calls to a different untrusted contract.
That old reentrancy bug bites again on Compound forks w/ $80M loss! This time around, it re-enters via exitMarket()!!! https://t.co/NpC8AAZRXc
Be careful, all Compound forks in EVM-compliant chains. Make contact with your auditors now or you can call us when we could be associated with a help pic.twitter.com/M9JElTWMSd
— PeckShield Corporation. (@peckshield) April 30, 2022
Security-focused ranking platform CertiK told Cointelegraph that the attacker has sent 5400 Ether (ETH), or $15,298,900 during the time of writing, to Tornado Cash but still holds 22,672.97 ETH, or $64,245,245.43 during the time of writing, within their wallet. The attack has drained funds in the Rari pool as the Fei Pools (Tribe, Curve) remain unaffected.
This past year on May 8, 2021, Rari Capital grew to become victim to some high-priced exploit which was associated with the combination with Alpha Venture DAO, formerly Alpha Finance Lab. At time of writing, there has been no official bulletins in the Fei Protocol team around the outcomes of their analysis.
Related: Arrange for $1M bug bounties and double the amount nodes in wake of $600M Ronin hack
Because the crypto community experiences a constantly evolving fight against online hackers, numerous projects and protocols have made the decision to amp up their safety measures. On Th, the Ronin Network and Sky Mavis revealed intends to upgrade their smart contracts — following a $600 million hack in the last month.
We’ve come up with a postmortem concerning the Ronin exploit that happened on March 23rd.
• Why it happened
• What we are doing to make certain this never happens again
• Ronin bridge re-opening updatehttps://t.co/FfwCtCG84E— Ronin (@Ronin_Network) April 27, 2022
The U . s . States Fbi (FBI) attributed the attack to North Korea-based and condition-backed hacking group Lazurus, because it fired off an alert with other crypto and blockchain organizations.


