Cybersecurity analyst Serpent has revealed his picks which are more dastardly crypto and nonfungible token (NFT) scams presently participating in Twitter.
The analyst, that has 253,400 supporters on Twitter, may be the founding father of artificial intelligence and community-powered crypto threat minimization system, Sentinel.
Inside a 19-part thread published on August. 21, Serpent outlined how scammers target unskilled crypto users by using copycat websites, URLs, accounts, hacked verified accounts, fake projects, fake airdrops and lots of adware and spyware.
One of the most worrisome strategies comes among a current spate of crypto phishing scams and protocol hacks. Serpent explains the Crypto Recovery Scam can be used by bad actors to trick individuals who’ve lately lost funds to some prevalent hack, stating:
“Simply put, they make an effort to target those who have recently been scammed, and state they recover the funds.”
Based on Serpent, these scammers tell you they are blockchain developers and look for users which have fallen victim to some recent large-scale hack or exploit, asking for a small fee to deploy a good contract that may recover their stolen funds. Rather, they “take the charge and run.”
It was observed in action following the multimillion-dollar exploit affecting Solana wallets earlier this year, with Heidi Chakos, the host from the YouTube funnel Crypto Tips, warning the city to take into consideration scammers supplying a solution towards the hack.
Another strategy also leverages recent exploits. Based on the analyst, the Fake Revoke.Cash Scam, methods users into going to a phishing website by warning them their crypto assets might be in danger, utilizing a “state of urgency” to obtain users to click on the malicious link.
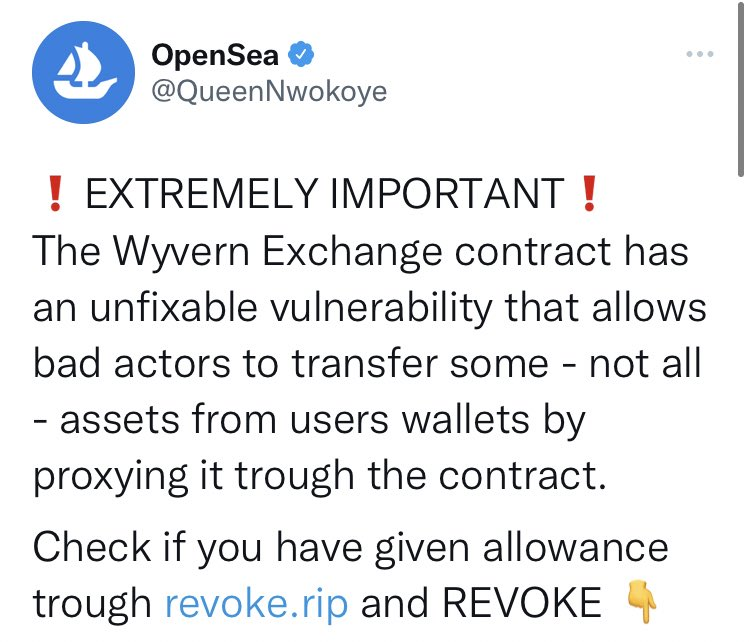
Another strategy uses Unicode Letters to create a phishing URL look almost the same as an authentic one, but replacing among the letters having a Unicode lookalike. Meanwhile, another strategy sees scammers hack a verified Twitter account, that is then renamed and accustomed to impersonate someone of influence to shill fake mints or airdrops.
The rest of the scams target users wanting to obtain a get-wealthy-quick plan. Including the Uniswap Front Running Scam, frequently viewed as junk e-mail bot messages telling users to look at a relevant video regarding how to “make $1400/DAY front-running Uniswap,” which rather methods them into delivering their to some scammer’s wallet.
Another strategy is actually a Honeypot Account, where users are supposedly leaked a personal key to get into a loaded wallet. But, once they make an effort to send crypto to be able to fund the change in coins, they’re immediately sent off to the scammers’ wallets using a bot.
Other tactics involve asking high-value NFT collectors to “beta test” a brand new play-to-earn (P2E) game or project or commissioning fake try to NFT artists. But, in the two cases, the trick is just a reason to transmit them malicious files that may scrape browser cookies, passwords and extension data.
Related: Aurora Labs professional details ‘fascinating and devious’ crypto scam he almost fell for
A week ago, a study from Chainalysis noted that revenue from crypto scams fell 65% in 2022 to date because of falling asset prices and also the exit of unskilled crypto users in the market. Total crypto scam revenue year-to-date is presently sitting at $1.6 billion, lower from roughly $4.6 billion within the prior year.


