Despite being underpinned by blockchain technology that promises security, immutability, and finish transparency, many cryptocurrencies like Bitcoin SV (BSV), Litecoin (LTC) and Ethereum Classic (ETC) have underwent 51% attacks several occasions previously. While there are lots of mechanisms through which malicious entities can and also have exploited blockchains, a 51% attack, or perhaps a majority attack because it is also known as, takes place when several miners or perhaps an entity controls greater than 50% from the blockchain’s hashing power after which assumes control of it.
Perhaps probably the most costly and tiresome approach to compromise a blockchain, 51% of attacks happen to be largely effective with smaller sized systems that need lower hashing capacity to overcome nearly all nodes.
Understanding a 51% attack
Before delving in to the technique involved with a 51% attack, you should know how blockchains record transactions, validate them and also the different controls baked into their architecture to avoid any alteration. Employing cryptographic strategies to connect subsequent blocks, which are records of transactions that occured around the network, a blockchain adopts 1 of 2 kinds of consensus mechanisms to validate every transaction through its network of nodes and record them permanently.
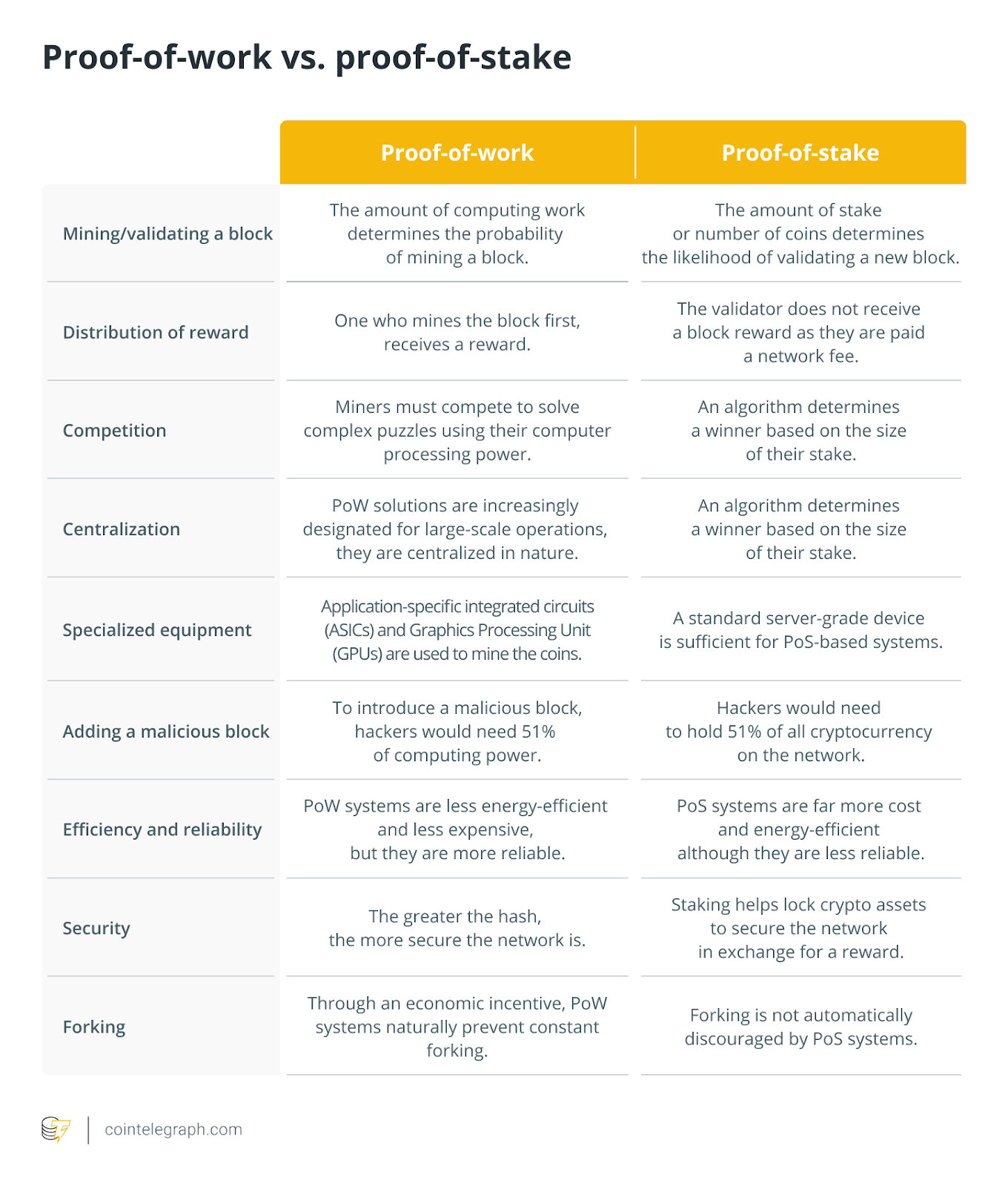
While nodes inside a proof-of-work (Bang) blockchain have to solve complex mathematical puzzles to be able to verify transactions and add these to the blockchain, a proof-of-stake (PoS) blockchain requires nodes to stake some the native token to earn validator status. In either case, a 51% attack could be orchestrated by manipulating the network’s mining hash rate or by commanding greater than 50% from the staked tokens within the blockchain.
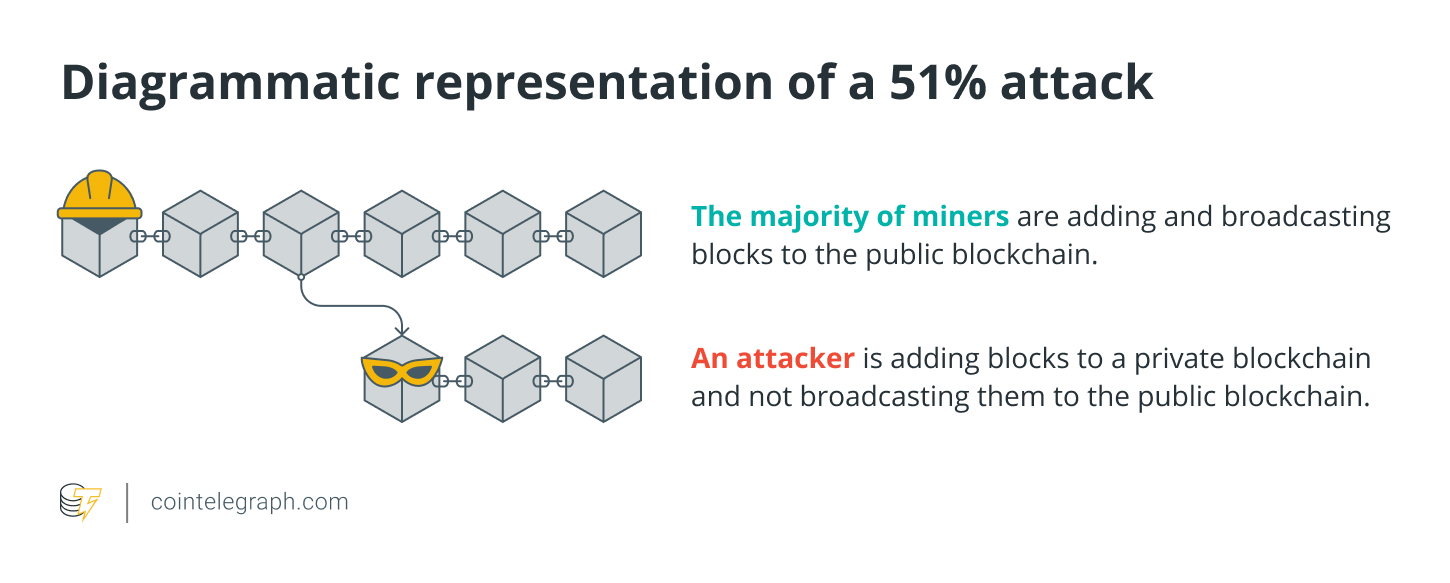
To know the way a 51% attack works, let’s suppose greater than 50% of all of the nodes that perform these validating functions conspire together introducing another form of the blockchain or perform denial-of-service (DOS) attack. The second is a kind of 51% attack where the remaining nodes are avoided from performing their functions as the attacking nodes start adding new transactions towards the blockchain or erasing original copies. Either in situation, the attackers may potentially reverse transactions as well as double-spend the native crypto token, that is similar to creating counterfeit currency.
Pointless to state, this type of 51% attack can compromise the whole network and not directly cause great losses for investors who contain the native token. Despite the fact that creating an altered form of the initial blockchain needs a phenomenally great deal of computing power or staked cryptocurrency within the situation of huge blockchains like Bitcoin or Ethereum, it’s not as far-fetched for smaller sized blockchains.
A DOS attack is capable of doing paralyzing the blockchain’s functioning and may negatively change up the underlying cryptocurrency’s cost. However, it’s improbable that older transactions beyond a particular cut-off could be reversed and therefore puts only the newest or future transactions made around the network in danger.
Is really a 51% attack on Bitcoin possible?
For any Bang blockchain, the prospect of a 51% attack decreases because the hashing power or even the computational power utilized per second for mining increases. Within the situation from the Bitcoin (BTC) network, perpetrators will have to control over fifty percent from the Bitcoin hash rate that presently is ~290 exahashes/s hashing power, requiring them to get into a minimum of single.3 million of the very most effective application-specific integrated circuit (ASIC) miners like Bitmain’s Antminer S19 Pro that retails for approximately $3,700 each.
This could entail that attackers have to purchase mining equipment totaling around $10 billion simply to stand an opportunity to perform 51% attack around the Bitcoin network. There are other aspects like discovered another means cheap they wouldn’t be titled to the mining rewards relevant for honest nodes.
However, for smaller sized blockchains like Bitcoin SV, the scenario is very different, because the network’s hash rate is around 590PH/s, making the Bitcoin network almost 500 occasions more effective than Bitcoin SV.
Within the situation of the PoS blockchain like Ethereum, though, malicious entities will have to have over fifty percent from the total Ether (ETH) tokens which are secured in staking contracts around the network. This could require vast amounts of dollars only when it comes to acquiring the requisite computing capacity to have some semblance of launching a effective 51% attack.
Furthermore, within the scenario the attack fails, all the staked tokens might be confiscated or locked, dealing a substantial financial blow towards the entities active in the purported attack.
How you can identify and stop a 51% attack on the blockchain?
The very first look for any blockchain is always to make sure that not one entity, number of miners or perhaps a mining pool controls greater than 50% from the network’s mining hashrate or even the final amount of staked tokens.
This involves blockchains to help keep a continuing check up on the entities active in the mining or staking process and take remedial action in situation of the breach. Regrettably, the Bitcoin Gold (BTG) blockchain couldn’t anticipate or stop this from happening in May 2018, with an identical attack repeating in The month of january 2020 that cause nearly $70,000 price of BTG being double-spent by a mystery actor.
In most these instances, the 51% attack was thanks to just one network attacker gaining control of greater than 50% from the hashing power after which proceeding to conduct deep reorganizations from the original blockchain that reversed completed transactions.
The repeated attacks on Bitcoin Gold do explain the significance of counting on ASIC miners rather of cheaper GPU-based mining. Since Bitcoin Gold uses the Zhash formula which makes mining possible even on consumer graphics cards, attackers are able to afford to produce a 51% attack on its network without requiring to take a position heavily within the more costly ASIC miners.
This 51% attack example does highlight the highest security controls provided by ASIC miners because they require a greater quantum of investment to obtain them and therefore are built particularly for the blockchain, which makes them useless for mining or attacking other blockchains.
However, when miners of cryptocurrencies like BTC shift to smaller sized altcoins, even a small amount of them may potentially control greater than 50% from the altcoin’s smaller sized network hashrate.
Furthermore, with providers for example NiceHash allowing individuals to rent hashing power for speculative crypto mining, the expense of launching a 51% attack could be drastically reduced. It has attracted focus on the requirement for real-time monitoring of chain reorganizations on blockchains to focus on a continuing 51% attack.
Durch Media Lab’s Digital Currency Initiative (DCI) is a such initiative which has built a method to positively monitor numerous Bang blockchains as well as their cryptocurrencies, reporting any suspicious transactions that could have double-spent the native token throughout a 51% attack.
Cryptocurrencies for example Hanacoin (HANA), Vertcoin (VTC), Verge (XVG), Expanse (EXP), and Litecoin Cash are only a couple of types of blockchain platforms that faced a 51% attack as stated by the DCI initiative.
Of these, the Litecoin Cash attack in This summer 2019 is really a classic illustration of a 51% attack on the proof-of-stake blockchain, although the attackers didn’t mine any new blocks and double-spent Litecoin Cash (LCC) tokens which were worth under $5,000 during the time of the attack.
This may highlight the low risks of 51% attacks on PoS blockchains, deeming them less appealing to network attackers, and is among the a lot of reasons to have an growing quantity of systems transitioning towards the PoS consensus mechanism.