Blockchain security firm BlockSec has debunked a conspiracy theory alleging the $160 million Wintermute hack was an internal job, noting the evidence employed for allegations is “not convincing enough.”
The 2009 week cyber sleuth James Edwards printed a study alleging the Wintermute smart contract exploit was likely conducted by someone with inside understanding from the firm, questioning activity concerning the compromised smart contract and 2 stablecoin transactions particularly.
BlockSec has since gone within the claims inside a Wednesday publish on Medium, suggesting the “accusation from the Wintermute project isn’t as solid because the author claimed,” including a Tweet:
“Our analysis implies that the report isn’t convincing enough to accuse the Wintermute project.
In Edward’s original publish, he basically came attention regarding the way the hacker could enact a lot carnage around the exploited Wintermute smart contract that “supposedly had admin access,” despite showing no proof of getting admin abilities throughout his analysis.
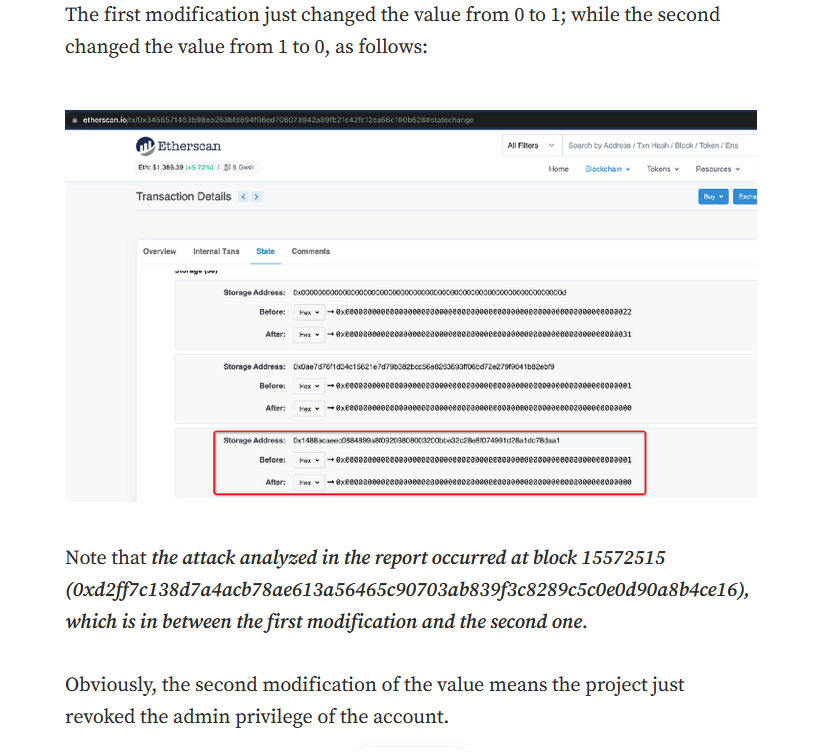
BlockSec however quickly debunked the claims, because it outlined that “the report just researched the present condition from the account within the mapping variable _setCommonAdmin, however, it’s not reasonable since the project might take actions to revoke the admin privilege after understanding the attack.”
Our short research into the Accusation from the Wintermute Project: https://t.co/6Lw6FjUrLp@wintermute_t @evgenygaevoy @librehash @WuBlockchain @bantg
Our analysis implies that the report isn’t convincing enough to accuse the Wintermute project.
— BlockSec (@BlockSecTeam) September 27, 2022
It pointed to Etherscan transaction details which demonstrated that Wintermute had removed admin rights once it grew to become conscious of the hack.
Edwards also asked why Wintermute had $13 million price of Tether (USDT) transferred from two or their accounts on two different exchanges for their smart contract just two minutes after it had been compromised, suggesting it had been foul play.
Related: Tribe DAO votes in support of repaying victims of $80M Rari hack
Addressing this, BlockSec contended that this isn’t as suspicious because it seems, because the hacker might have been monitoring Wintermute transferring transactions, possibly via bots, to swoop inside.
“However, it’s not as plausible because it claimed. The attacker could monitor the game from the transferring transactions to offer the goal. It’s not quite weird from the technical perspective. For instance, there are some on-chain MEV-bots which continuously monitor the transactions to create profits.”
As formerly mentioned in Cointelegraph’s first article around the matter, Wintermute has strongly refuted Edwards claims, and it has stated that his methodology is filled with inaccuracies.


