2022 is a lucrative year for online hackers preying around the nascent Web3 and decentralized finance (DeFi) spaces, using more than $2 billion price of cryptocurrency fleeced in a number of high-profile hacks up to now. Mix-chain protocols happen to be particularly hard hit, with Axie Infinity’s $650 million Ronin Bridge hack comprising a substantial part of stolen funds this season.
The pillaging ongoing in to the other half of 2022 as mix-chain platform Nomad saw $190 million drained from wallets. The Solana ecosystem was the following target, with online hackers accessing the non-public keys of some 8000 wallets that led to $5 million price of Solana (SOL) and Solana Program Library (SPL) tokens being pilfered.
deBridge Finance were able to sidestep an attempted phishing attack on Monday, August. 8, unpacking the techniques utilized by exactly what the firm suspects is a huge-varying attack vector utilized by North Korean Lazarus Group online hackers. Only a couple of days later, Curve Finance endured an exploit that saw online hackers reroute users to some counterfeit website that led to the thievery of $600,000 worth of USD Gold coin (USDC).
Multiple points of failure
They at deBridge Finance offered some pertinent insights in to the prevalence of those attacks in correspondence with Cointelegraph, considering that numerous their team people formerly labored for any prominent anti-virus company.
Co-founder Alex Smirnov highlighted the driving factor behind the targeting of mix-chain protocols, given their role as liquidity aggregators that fulfill mix-chain value transfer demands. Many of these protocols turn to aggregate just as much liquidity as you possibly can through liquidity mining along with other incentives, that has inevitably be a honey-pot for dubious actors:
“By locking a lot of liquidity and unintentionally supplying an assorted group of available attack methods, bridges are earning themselves a target for online hackers.”
Smirnov added that bridging protocols are middleware that depends on the safety models of all of the supported blockchains that they aggregate, which drastically boosts the potential attack surface. This alsmakes it easy to perform a panic attack in a single chain to attract liquidity from others.
Related: What is the secure future for mix-chain bridges?
Smirnov added the Web3 and mix-chain space is a duration of nascence, by having an iterative procedure for development seeing teams study from others’ mistakes. Drawing parallels towards the first couple of years within the DeFi space where exploits were rife, the deBridge co-founder conceded this would be a natural teething process:
“The mix-chain space is very youthful even inside the context of Web3, so we’re seeing this same process engage in. Mix-chain has tremendous potential which is inevitable more capital flows in, and online hackers allocate additional time and sources to locating attack vectors.”
The Bend Finance DNS hijacking incident also illustrates the range of attack methods open to dubious actors. Bitfinex chief technology officer Paolo Ardoino told Cointelegraph the must be on guard against all security threats:
“This attack demonstrates once more the resourcefulness of online hackers presents an almost and ever-present danger to the industry. The truth that a hacker has the capacity to alter the DNS entry for that protocol, forwarding users to some fake clone and approving a malicious contract states a great deal for that vigilance that must definitely be worked out.”
Stemming the tide
With exploits becoming rife, projects won’ doubt be thinking about methods to mitigate these risks. The reply is not even close to obvious-cut, because of the variety of avenues attackers have available. Smirnov likes to utilize a “swiss cheese model” when conceptualizing the safety of bridging protocols, with the only method to execute a panic attack is that if numerous “holes” momentarily fall into line.
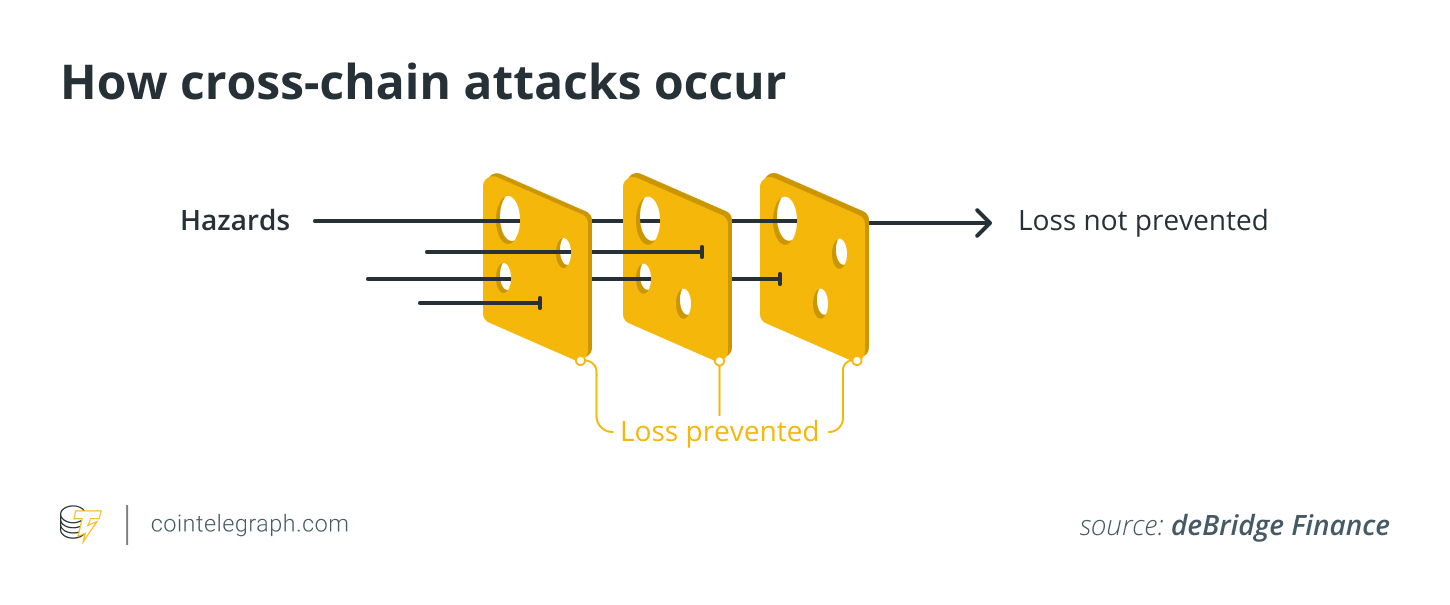
“In order to help make the degree of risk minimal, how big the opening on every layer ought to be aimed to become as minimal as you possibly can, and the amount of layers ought to be maximized.”
Again this can be a complicated task, because of the moving parts involved with mix-chain platforms. Building reliable multilevel security models requires comprehending the diversity of risks connected with mix-chain protocols and also the perils of supported chains.
The main threats include vulnerabilities using the consensus formula and codebase of supported chains, 51% attacks and blockchain reorganizations. Risks towards the validation layers could range from the collusion of validators and compromised infrastructure.
Software development risks will also be another consideration with vulnerabilities or bugs in smart contracts and bridge validation nodes key regions of concern. Lastly, deBridge notes protocol management risks for example compromised protocol authority keys as the second security consideration.
“All these risks are rapidly compounded. Projects must take a multi-faceted approach, and additionally to security audits and bug bounty campaigns, lay various safety measures and validations in to the protocol design itself.”
Social engineering, more generally known as phishing attacks, is yet another indicate consider. As the deBridge team were able to thwart this kind of attack, still it remains probably the most prevalent threats towards the wider ecosystem. Education and strict internal security coverage is fundamental to avoid falling prey to those cunning tries to steal credentials and hijack systems.


