The explosiveness and dollar worth of nonfungible tokens (NFTs) appear either to draw attention away from investors from upping their operational security to prevent exploits, or online hackers are merely following a money and taking advantage of very complex ways of exploit collectors’ wallets.
A minimum of, it was the situation for me personally long ago when once i fell for any classic message delivered to me over Discord that caused me to gradually but very rapidly lose my best assets.
The majority of the scams on Discord occur in an exceedingly similar fashion in which a hacker requires a roster of people around the server after which transmits direct messages for them hoping they’ll bite in the bait.
BEWARE: Several scams happening on Discord tonight. QUESTION EVERYTHING. Before hitting links, quadruple check who it’s from and when it’s legitimate. Then check 12 more occasions on Twitter via reliable sources.
— Farokh (@farokh) October 27, 2021
“It transpires with the very best of us,” aren’t the language you need to hear with regards to a hack. Listed here are the very best three a few things i learned from my experience regarding how to double-on security, beginning with minimizing using a hot wallet and just ignoring DM’d links
A fast quick studies in hardware wallets
After my hack, I had been immediately advised and that i cannot reiterate it enough, never share your seed phrase. Nobody ought to be requesting it. I additionally found that I possibly could no more forego security in the privilege of convenience.
Yes, hot wallets tend to be more seamless and faster to do business with, but they don’t have the additional security of the pin along with a passphrase like they are doing on the hardware, or cold, wallet.
Hot wallets like MetaMask and Coinbase are connected to the web, causing them to be more susceptible and prone to hacks.
Unlike hot wallets, cold wallets are applications or devices whereby the user’s private keys are offline and don’t connect to the web. Given that they operate offline, hardware wallets prevent unauthorized access, hacks and typical vulnerabilities by systems, a thing that are inclined to when they’re online.
4/ Make Use Of A HARDWARE WALLET
A hardware based wallet stores the keys from your primary device. Your device that may have adware and spyware, key loggers, screen capture devices, file inspectors, that may be snooping for the keys.
I suggest a Ledger Nano Shttps://t.co/LoT5lbZc0L
— richerd.eth (マ,マ) gm NFT.New york city (@richerd) Feb 2, 2022
Moreso, hardware wallets allow users to setup an individual pin to unlock their hardware wallet and make up a secret passphrase like a bonus layer of security. Now, a hacker not just must know one’s recovery phrase and pin but additionally a passphrase to verify a transaction.
Pass-phrases aren’t as discussed as seed phrases because most users might not make use of a hardware wallet or know about the mysterious passphrase.
Use of a seed phrase will unlock some wallets that corresponds by using it, however a passphrase also has the ability to complete exactly the same.
How can pass-phrases work?
Passphrases are in lots of ways extra time of one’s seed phrase because it mixes the randomness from the given seed phrase using the personal input from the user to compute an entire different group of addresses.
Consider passphrases being an capability to unlock an entire group of hidden wallets on the top from the ones already generated through the device. There’s no such factor being an incorrect passphrase as well as an infinite amount could be produced. In this manner, users can go that step further and make decoy wallets as plausible deniability to diffuse any potential hack from targeting one primary wallet.
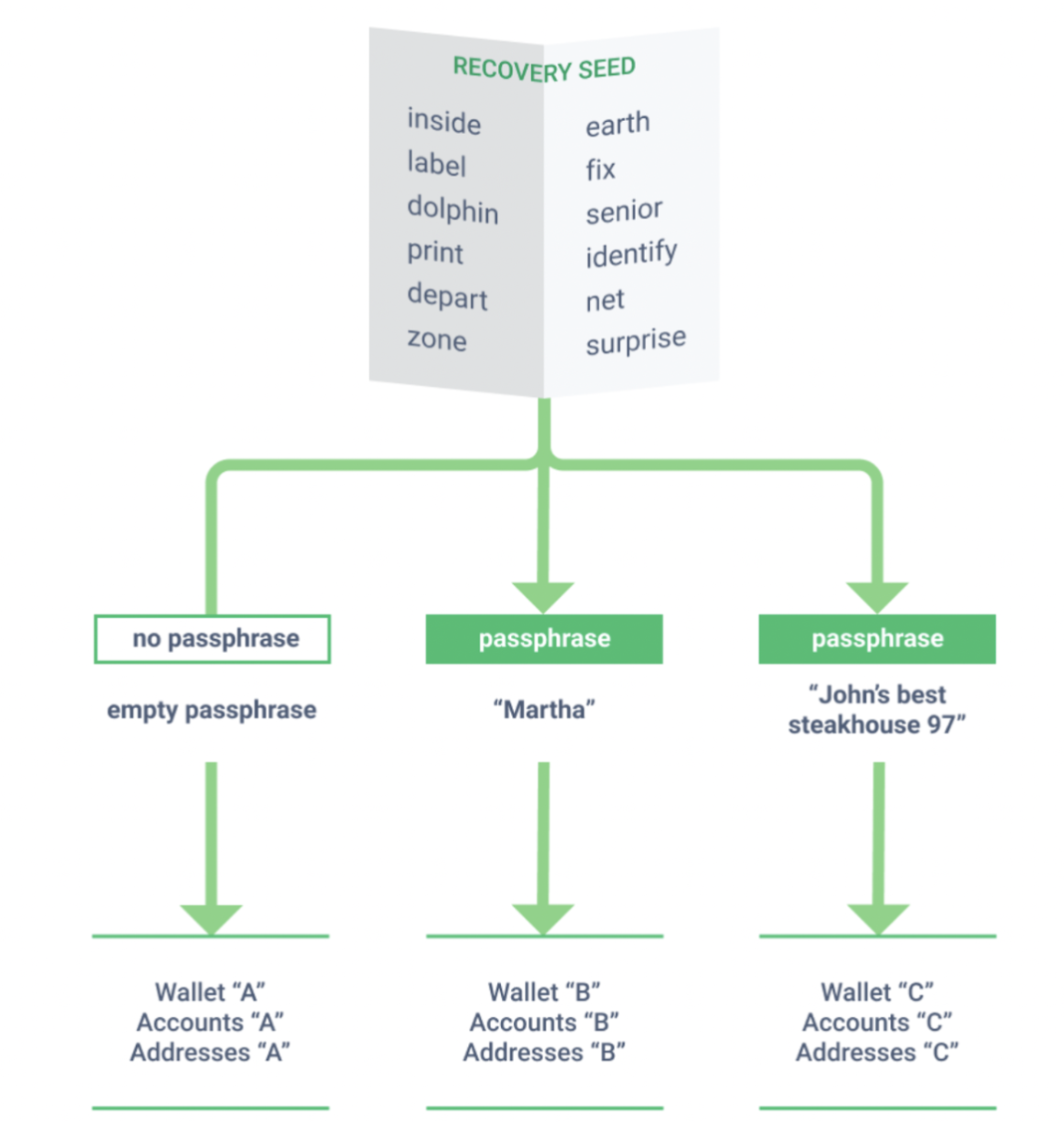
This selection is advantageous when separating one’s digital assets between accounts but terrible if forgotten. The only method for any user to gain access to the hidden wallets frequently is as simple as inputting the precise passphrase, character by character.
Much like one’s seed phrase, a passphrase shouldn’t are exposed to any mobile or online device. Rather, it ought to be stored in writing and stored somewhere secure.
How to setup a passphrase on Trezor
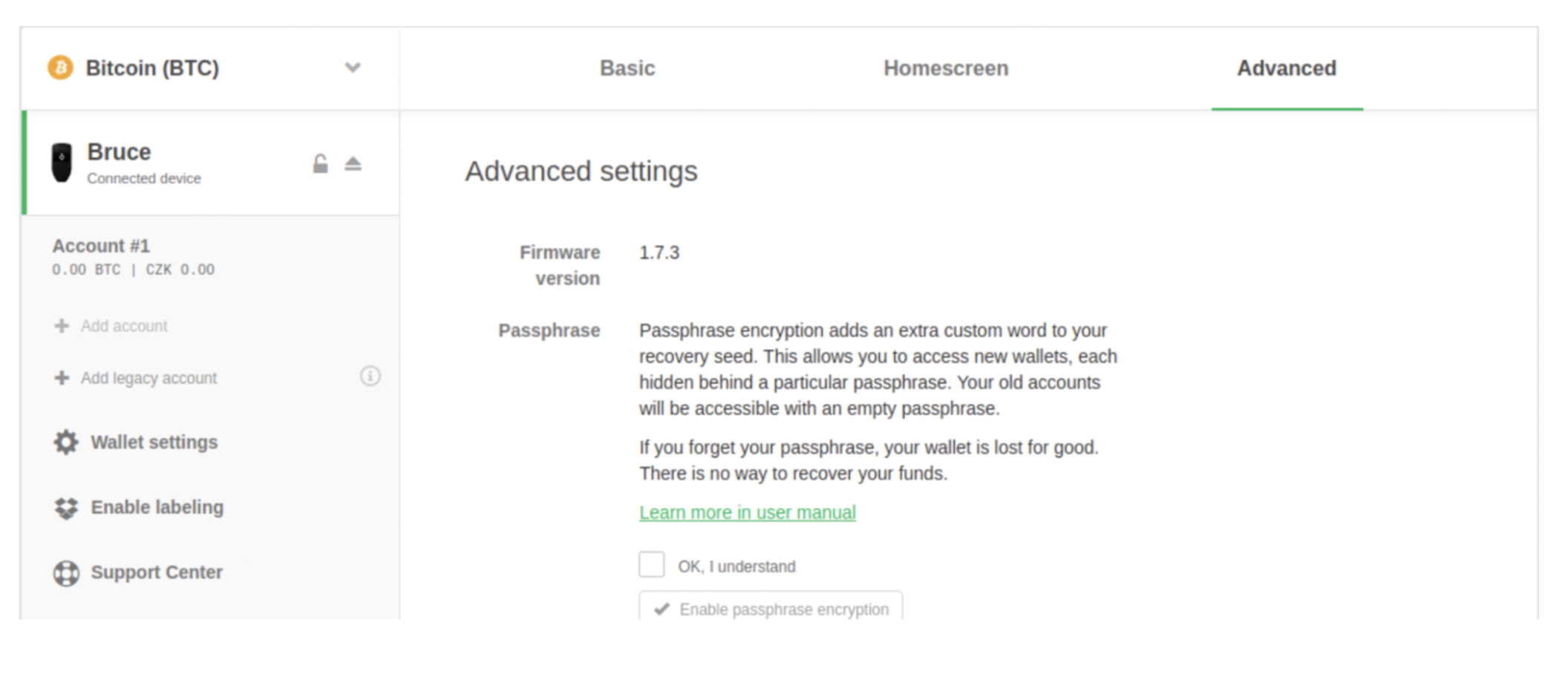
When a hardware wallet is installed, connected and unlocked, users who wish to let the feature can perform so in 2 ways. When the user is within their Trezor wallet, they’ll press the “Advanced settings” tab, where they will discover a box to check on off and away to let the passphrase feature.
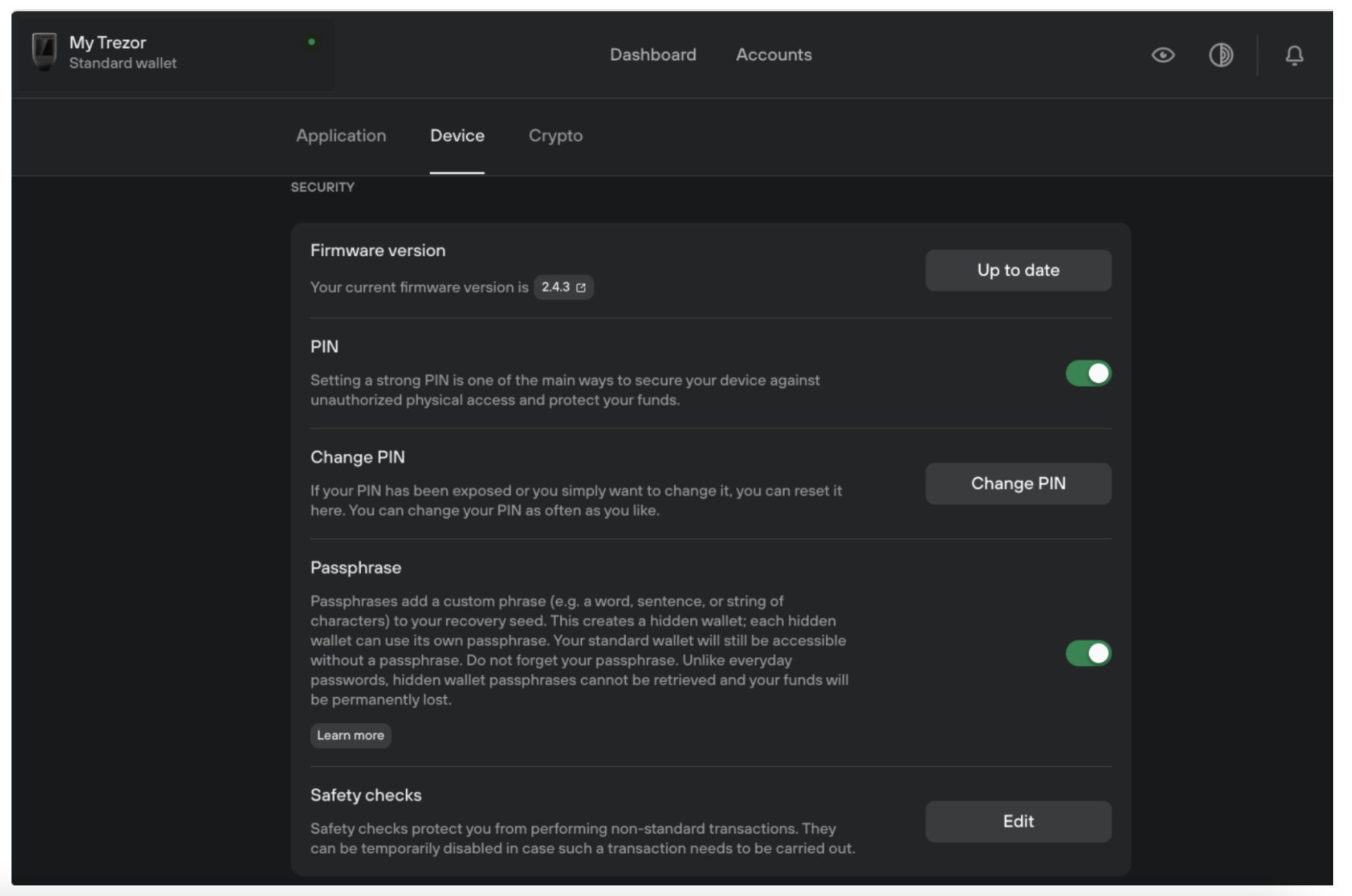
Similarly, users can let the feature if they’re within the Trezor suite, where they may also find out if their firmware expires-to-date as well as their pin installed.
There’s two different Trezor models, Trezor One and Trezor Model T, each of which enable users to activate passphrases just diversely.
The Trezor Model One only offers users the choice to key in their passphrase on the internet browser which isn’t perfect in case the computer is infected. However, the Trezor Model T enables users the choice to make use of the device’s touchscreen pad to type the passphrase or types inside the internet browser.
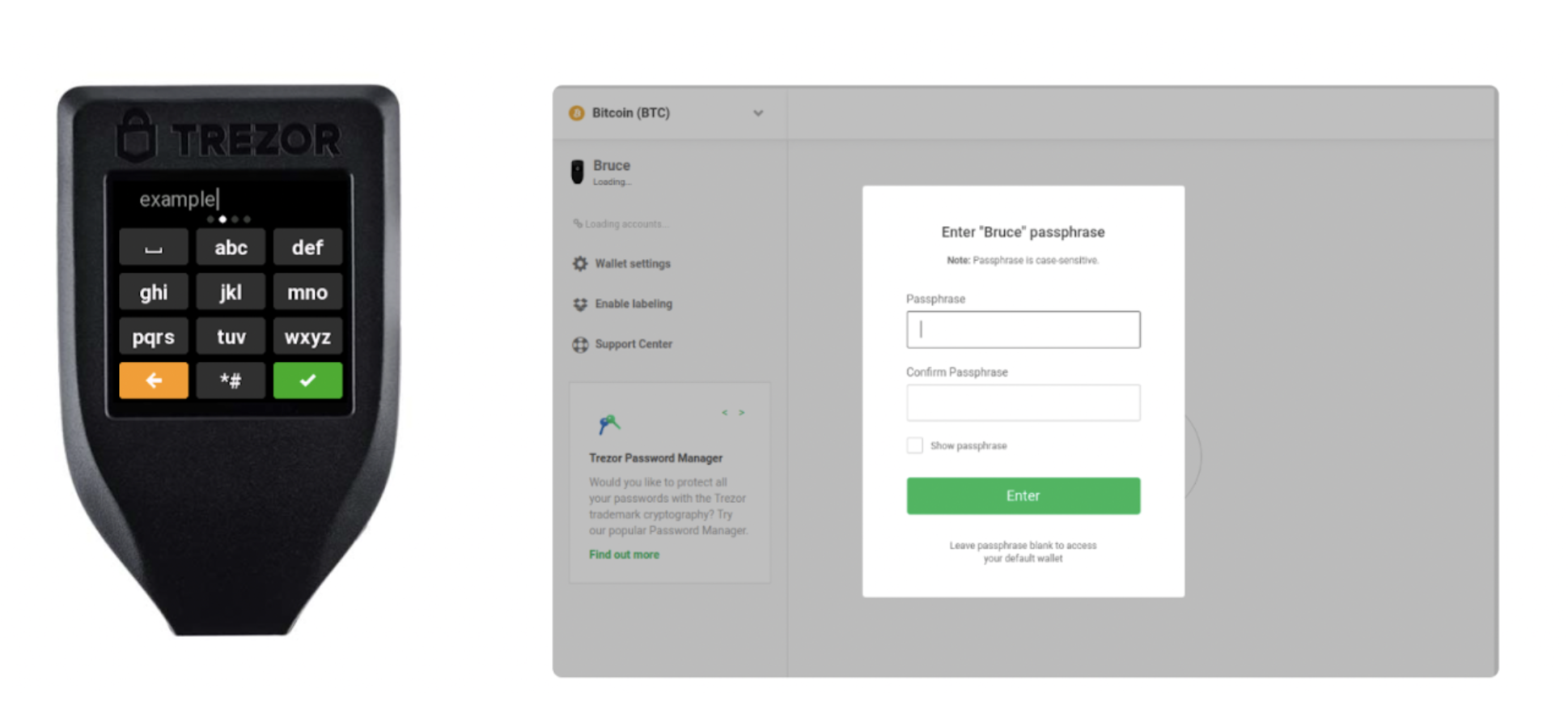
On models, following the passphrase is joined, it’ll show up on the device’s screen, waiting for confirmation.
The switch side to security
You will find risks to security, even though it sounds counterproductive. Why is the passphrase so strong like a next step of authentication towards the seed phrase is what causes it to be vulnerable. If forgotten or lost, the assets are just like gone.
Sure, these extra layers of security take some time and also the extra precaution and could appear a little outrageous, but my experience would be a hard lesson in taking responsibility to make sure each asset was safe and sound.
The views and opinions expressed listed here are exclusively individuals from the author and don’t always reflect the views of Cointelegraph.com. Every investment and buying and selling move involves risk, you need to conduct your personal research when making the decision.


